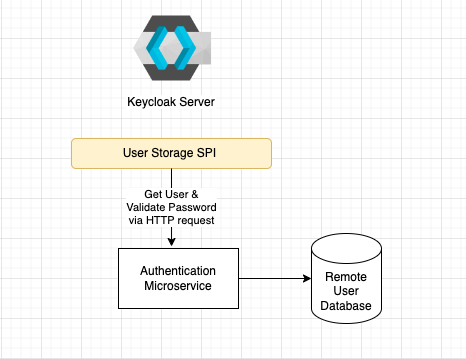
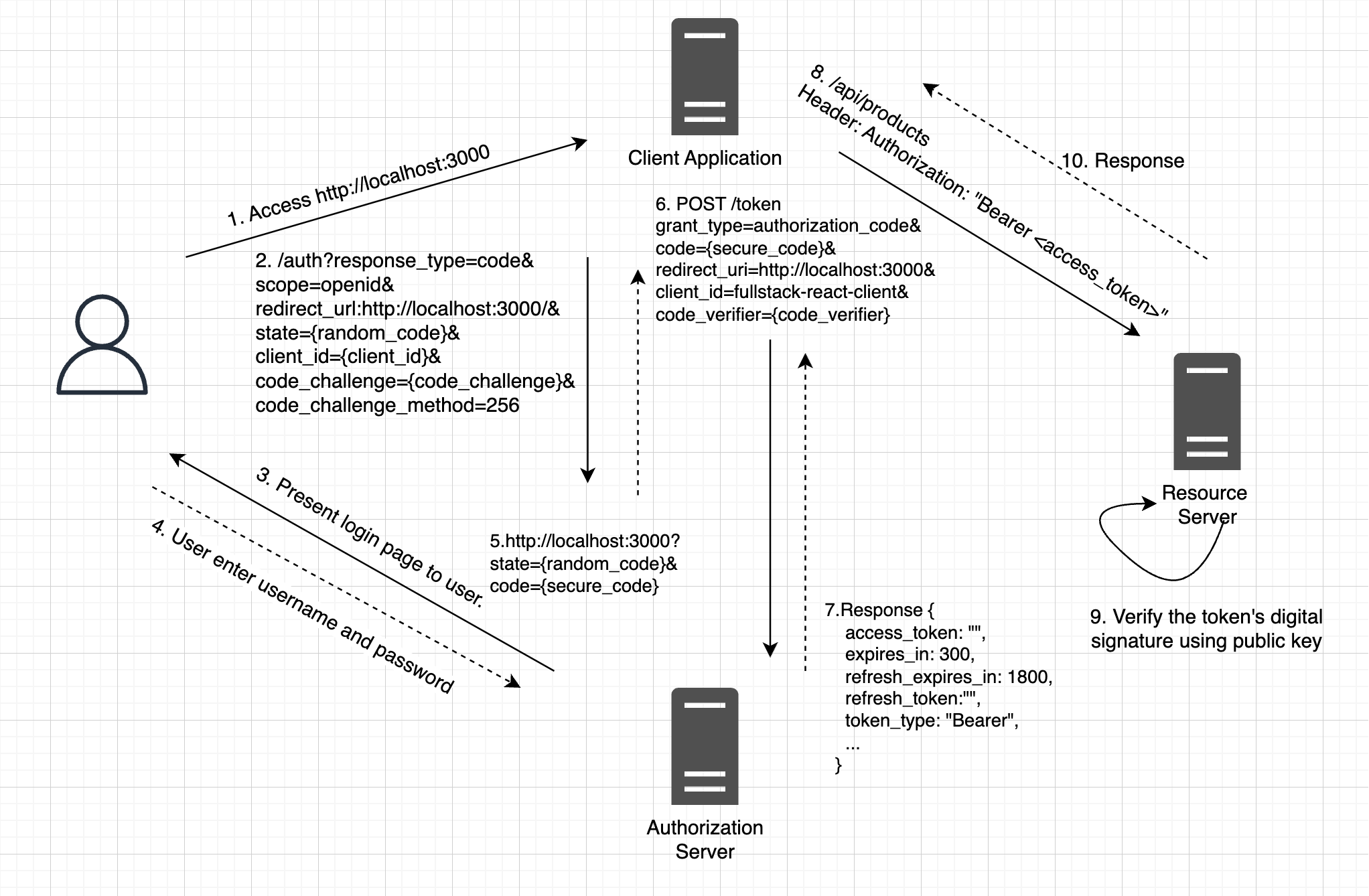
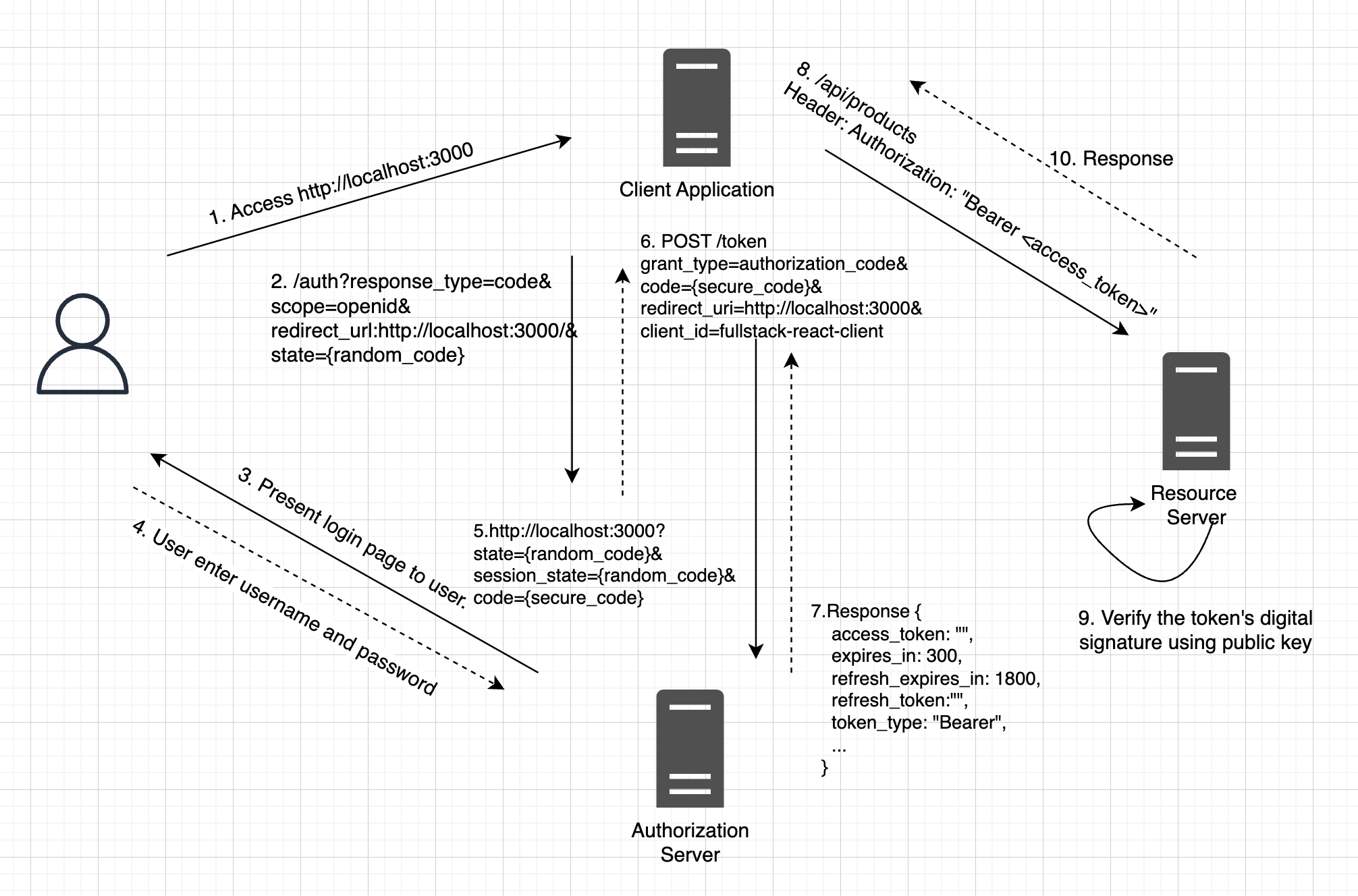
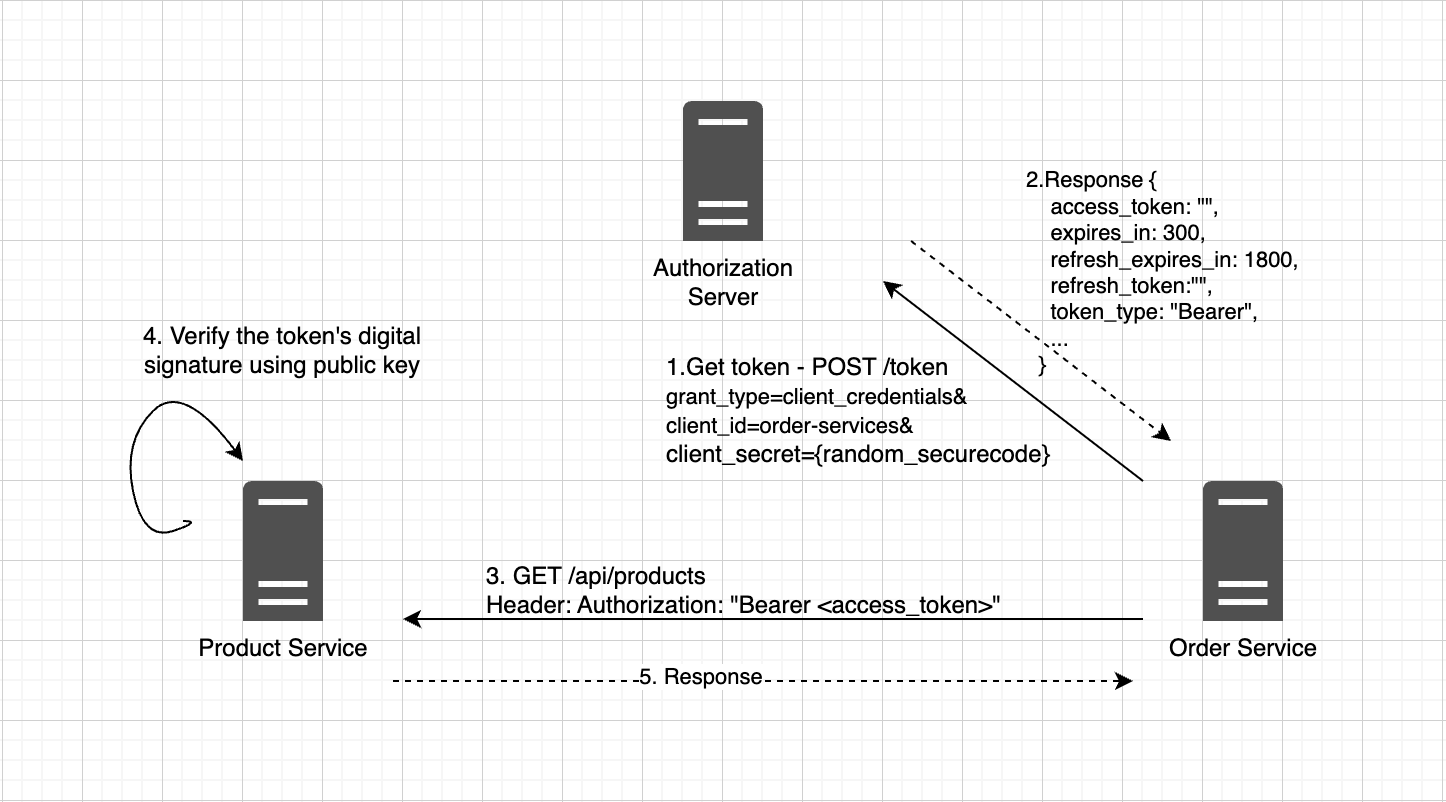
In this article, we'll explore how to authenticate users in Keycloak using a custom User Storage SPI provider. This integration enables seamless authentication and management of users stored in an…
How To: Keycloak Remote User Authentication Using User Storage SPI